[[{“value”:”
A vulnerability, CVE-2023-36049 has been identified in the Microsoft .NET Framework and Visual Studio, posing a serious threat to the integrity of FTP servers.
If exploited, this flaw could allow attackers to write or delete files, compromising the security of applications and data.
The .NET Framework, a cornerstone of software development on Microsoft Windows, facilitates the creation and execution of applications within a managed execution environment.
However, a flaw in its design related to handling FTP commands has opened a door for cyber attackers.
FTP, or File Transfer Protocol, is a standard network protocol for transferring computer files between a client and server on a computer network.
It operates on a dual-connection system, one for commands and the other for data transfer.
The vulnerability stems from the .NET Framework’s improper user input validation, specifically in how FTP command parameters and FTP URI requests are processed.
FTP commands have the following syntax:
<command> <SP> [parameters] <CRLF>
Vulnerability Unveiled
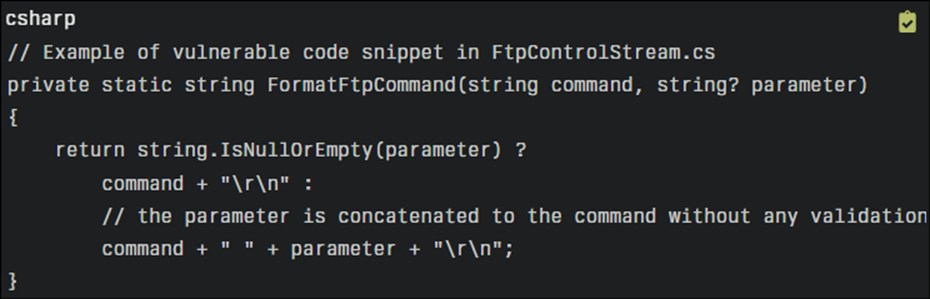
A detailed analysis reveals that the flaw is due to the .NET Framework’s FtpControlStream class, which inadequately validates FTP command parameters, allowing attackers to inject malicious commands.
For instance, when handling parameters that include Carriage Return Line Feed (CRLF) characters, the system fails to properly sanitize the input, leading to potential unauthorized file operations.
Source code snippet illustrating the vulnerability
The Trend Micro Research Team recently uncovered a vulnerability in .NET Framework and Visual Studio, allowing privilege escalation.
Document
Integrate ANY.RUN in your company for Effective Malware Analysis
Are you from SOC and DFIR teams? – Join With 400,000 independent Researchers
Malware analysis can be fast and simple. Just let us show you the way to:
Interact with malware safely
Set up virtual machine in Linux and all Windows OS versions
Work in a team
Get detailed reports with maximum data
If you want to test all these features now with completely free access to the sandbox: ..
Justin Hung and Yazhi Wang of the team have detailed the issue in a report through the Trend Micro Vulnerability Research Service.
The vulnerability has since been patched. Attackers can exploit this vulnerability by sending specially crafted requests to FTP servers.
Successful exploitation could enable unauthorized individuals to write or delete files on the server, potentially leading to data loss, data corruption, or unauthorized access to sensitive information.
The attack vector is particularly concerning for applications that rely on the .NET Framework for FTP operations.
Given the widespread use of the .NET Framework in enterprise environments, this vulnerability has a significant potential impact.
Mitigation and Response
Microsoft has responded to this critical vulnerability by releasing a patch.
The update addresses the flaw by improving the validation process for FTP command parameters and URI requests.
Administrators and developers must apply this patch promptly to protect their systems from potential attacks.
For those unable to apply the patch immediately, a temporary mitigation strategy involves refusing FTP URIs from untrusted sources and filtering FTP traffic to detect and block suspicious activity.
Monitoring FTP traffic for multiple commands sent in a single packet can help identify attempts to exploit this vulnerability, although this approach may yield false positives in regular traffic.
The discovery of this vulnerability underscores the importance of rigorous input validation in software development.
Maintaining the security of software frameworks and applications as cyber threats evolve is paramount.
Users and administrators are urged to apply the provided patch and follow best practices for network security to safeguard against potential exploits.
You can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits, with Perimeter81 malware protection. All are incredibly harmful, can wreak havoc, and damage your network.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
The post Microsoft .NET Framework & Visual Studio Flaw Let Attackers Write or Delete Files appeared first on Cyber Security News.
“}]] Read More
Cyber Security News


