Building cyber skills and roles from CyBOK foundations

The all in one place for non-profit security aid.

The Week in Ransomware – November 17th 2023 – Citrix in the Crosshairs
Ransomware gangs target exposed Citrix Netscaler devices using a publicly available exploit to breach large organizations, steal data, and encrypt files. […] Read More
BleepingComputer
FBI Releases Internet Crime Report for 2023 : 22% Surge Compared to 2022
[[{“value”:”
Federal Bureau of Investigation (FBI) has published its annual Internet Crime Report for 2023, highlighting a significant 22% increase in losses due to cybercrime, amounting to over $12.5 billion
This surge underscores cyber criminals’ growing sophistication and audacity in exploiting digital vulnerabilities.
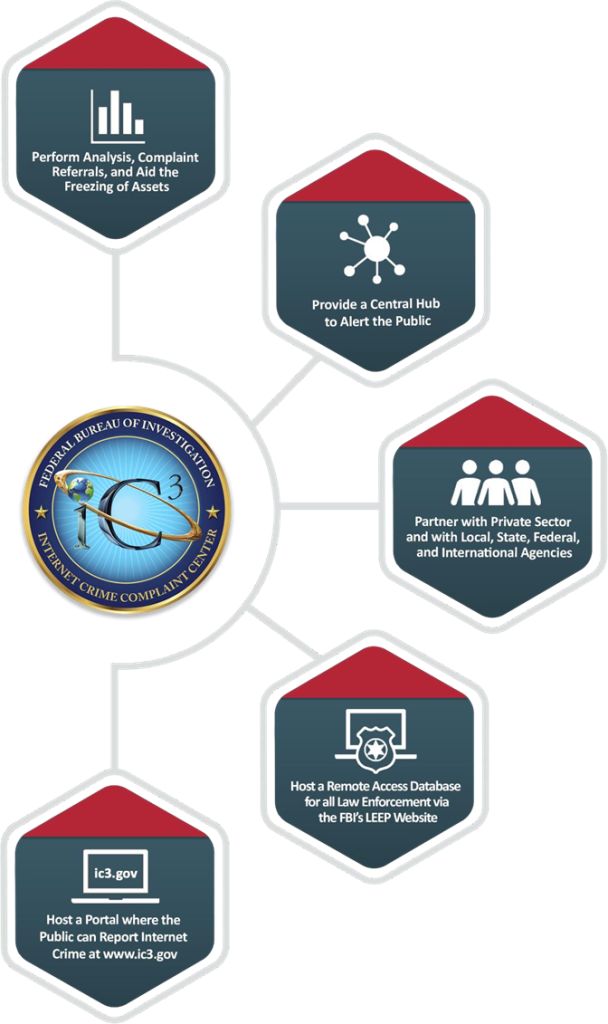
The Internet Crime Complaint Center (IC3), a pivotal arm of the FBI dedicated to combating cybercrime, registered an unprecedented 880,418 complaints from the American public in 2023.
This figure marks a nearly 10% increase in the number of complaints received and represents a staggering 22% rise in financial losses compared to the previous year.
Timothy Langan, Executive Assistant Director at the FBI, emphasized the conservative nature of these figures, suggesting the actual scope of cybercrime is likely much broader.
Document
Integrate ANY.RUN in your company for Effective Malware Analysis
Are you from SOC and DFIR teams? – Join With 400,000 independent Researchers
Malware analysis can be fast and simple. Just let us show you the way to:
Interact with malware safely
Set up virtual machine in Linux and all Windows OS versions
Work in a team
Get detailed reports with maximum data
If you want to test all these features now with completely free access to the sandbox: ..
The IC3 serves as a central hub for victims to report cybercrime and for the FBI to collect data, advance investigations, and identify changes in the threat landscape.
Since its inception in May 2000, the IC3 has received over eight million complaints. It is pivotal in the FBI’s intelligence-driven, threat-focused approach to protecting Americans from cyber-attacks and major criminal threats.
In 2023, ransomware incidents saw an 18% increase in complaints, with reported losses soaring by 74% from $34.3 million in 2022 to $59.6 million.
Cybercriminals continue evolving tactics, deploying multiple ransomware variants against the same victim and using data-destruction methods to pressure negotiations.
BEC scams remained a significant threat in 2023, with 21,489 complaints leading to over $2.9 billion in adjusted losses.
This sophisticated scam targets businesses and individuals by compromising legitimate business email accounts to conduct unauthorized fund transfers.
Investment fraud was the costliest crime type tracked by the IC3 in 2023, with losses climbing from $3.31 billion in 2022 to $4.57 billion—a staggering 38% increase.
Victims aged 30 to 49 were the most likely to report losses from investment scams.
The IC3’s RAT, established in 2018, has been instrumental in freezing funds for victims of cybercrime.
In 2023, the RAT initiated the Financial Fraud Kill Chain (FFKC) on 3,008 incidents, successfully placing a hold on $538.39 million out of potential losses of $758.05 million, marking a 71% success rate.
In New York, a critical infrastructure entity reported a $50 million loss due to a BEC incident.
The RAT’s swift action resulted in $44,936,460 being frozen and recovered.
A Connecticut individual nearly lost $426,000 in a real estate transaction due to a BEC scam. The RAT’s intervention enabled the freezing and return of $425,000, allowing the real estate transaction to proceed.
The FBI emphasizes the importance of public reporting in combating cybercrime.
Each report contributes to the FBI’s efforts to pursue adversaries, share intelligence, and protect citizens.
Cybersecurity is described as the ultimate team sport, with the FBI committed to working alongside the American public to defeat cyber adversaries.
As cyber threats evolve, the FBI remains committed to working alongside the American public and its partners to safeguard digital spaces and prosecute cybercriminals.
The 2023 Internet Crime Report highlights the challenges ahead and the strides made in combating the scourge of cybercrime.
You can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits, with Perimeter81 malware protection. All are incredibly harmful, can wreak havoc, and damage your network.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
The post FBI Releases Internet Crime Report for 2023 : 22% Surge Compared to 2022 appeared first on Cyber Security News.
“}]] Read More
Cyber Security News
