Michigan healthcare system succumbs to phishing scam. Meta temporarily banned from tracking Norwegian user behavioral data. Read More
The CyberWire
The all in one place for non-profit security aid.
Michigan healthcare system succumbs to phishing scam. Meta temporarily banned from tracking Norwegian user behavioral data. Read More
The CyberWire

North Korean State-Sponsored Hackers Suspected in JumpCloud Supply Chain Attack
An analysis of the indicators of compromise (IoCs) associated with the JumpCloud hack has uncovered evidence pointing to the involvement of North Korean state-sponsored groups, in a style that’s reminiscent of the supply chain attack targeting 3CX.
The findings come from SentinelOne, which mapped out the infrastructure pertaining to the intrusion to uncover underlying patterns. It’s worth noting Read More
The Hacker News | #1 Trusted Cybersecurity News Site
Ransomware Actor Exploited CoinMiner Attacker’s Proxy Server
Hackers can hide their names and access blocked websites or networks by using proxy servers, which help make these systems anonymous.
Compromised proxy servers can be employed as pipes for launching attacks, circulating malicious software, and engaging in illegal activities while covering up the actual origins of traffic.
There is also a risk of further infiltration into the network through any proxy server where vulnerabilities have been found.
Cybersecurity researchers at ASEC recently discovered that a ransomware actor exploited the proxy server of a CoinMiner attacker.
With ANYRUN You can Analyze any URL, Files & Email for Malicious Activity : Start your Analysis
Cyberattacks target not just companies but threat actors themselves.
A CoinMiner group’s proxy server used to control an infected botnet was exposed, allowing a ransomware actor’s RDP scan attack to infiltrate and infect the botnet with ransomware.
The initial CoinMiner breach likely involved scanning for MS-SQL server administrator (sa) accounts, using xp_cmdshell to install a backdoor downloading the CoinMiner malware from a C2 server.
This demonstrates how the infrastructures of threat actors can become compromised targets themselves.
An exposed reverse RDP proxy server was set up by the CoinMiner group using a modified Fast Reverse Proxy tool to enter their infected bots.
However, this exposed proxy server became a target for an RDP port scanning and brute force attack launched by ransomware actors.
The absence of login restrictions allowed the ransomware actor to gain admin access via the proxy and then move laterally before distributing ransomware throughout the CoinMiner botnet and network with tools.
CoinMiner is a threat actor to whom, for a specific ransomware attacker, it could have been either deliberate or coincidental that his RDP scan attack included using a proxy server.
The proxy server was just another target with an exposed RDP port, as the ransomware actor had seen it accidentally.
Since systems that had been compromised previously are more likely to contain vulnerabilities this time around, the ransomware actor decided to target systems attacked by other actors, which the attacker knew very well were proxies.
The repeated access into the affected system attached to the proxy suggests that the ransomware actor may have noticed strange behavior, indicating they were traversing between compromised systems.
Usually, rather than directly targeting and exploiting other actors’ infrastructure, threat actors trade credentials, malware, and services on dark web markets.
However, when assessing the attacks that use compromised infrastructures of other actors unknowingly, it is not easy to tell apart which individual behaviors and intentions are involved within this scenario.
If such cases become more common, threat actors may begin intentionally hacking each other’s infrastructure to launch more effective attacks by leveraging these systems and resources.
There is an emerging trend in which different groups of actors purposely infiltrate rival groups’ infrastructure, which could considerably complicate attribution and defense.
Looking for Full Data Breach Protection? Try Cynet’s All-in-One Cybersecurity Platform for MSPs: Try Free Demo
The post Ransomware Actor Exploited CoinMiner Attacker’s Proxy Server appeared first on Cyber Security News.
New Facebook photo rule hoax spreads
[[{“value”:”
Some hoaxes on Facebook are years old, but like a cat with nine lives they keep coming back again and again. This is certainly the case with this most recent hoax.
Fact-checking site Snopes is reporting on a hoax that concerns Meta’s use of our photos, messages and other posts on Facebook. Users are told in numerous ways to repost something that contains the phrase:
“I do not authorize META, Facebook or any entity associated with Facebook to use my photos, information, messages or posts, past or future.”
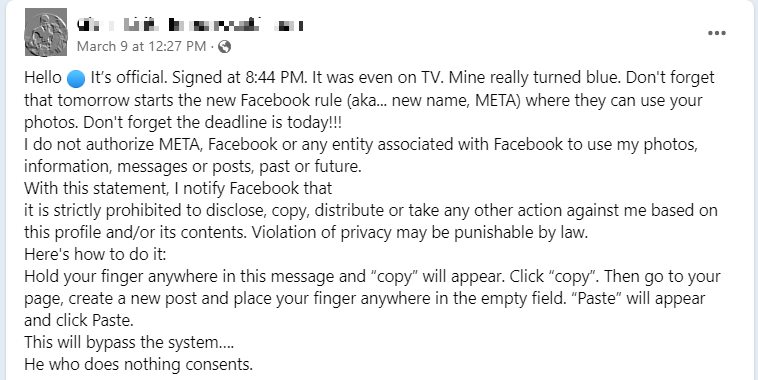
“Hello It’s official. Signed at 8:44 PM. It was even on TV. Mine really turned blue. Don’t forget that tomorrow starts the new Facebook rule (aka… new name, META) where they can use your photos. Don’t forget the deadline is today!!!
I do not authorize META, Facebook or any entity associated with Facebook to use my photos, information, messages or posts, past or future.
With this statement, I notify Facebook that
it is strictly prohibited to disclose, copy, distribute or take any other action against me based on this profile and/or its contents. Violation of privacy may be punishable by law.
Here’s how to do it:
Hold your finger anywhere in this message and “copy” will appear. Click “copy”. Then go to your page, create a new post and place your finger anywhere in the empty field. “Paste” will appear and click Paste.
This will bypass the system….
He who does nothing consents.”
The first round of hoax posts similar to this one surfaced in 2012 (and have resurfaced many times since then). As you can see in this page on the Internet archives, Facebook even issued a statement about it:
“Fact Check
Copyright Meme Spreading on Facebook
There is a rumor circulating that Facebook is making a change related to ownership of users’ information or the content they post to the site. This is false. Anyone who uses Facebook owns and controls the content and information they post, as stated in our terms. They control how that content and information is shared. That is our policy, and it always has been.”
With all the—legitimate—concern around keeping personal data private, one can see why people fall for hoaxes like this. However, this copy-paste post does nothing. Facebook doesn’t get to “own” your content and you don’t need to make any declarations about copyright issues since the law already protects you.
Equally, Facebook users cannot retroactively negate any of the privacy or copyright terms they agreed to when they signed up for their accounts, simply by posting a contrary legal notice on to Facebook.
In other words, you agreed to Facebook’s terms of use and when you did, you provided Facebook with a right to use, distribute, and share the things you post, subject to the terms and applicable privacy settings. If that doesn’t sit well with you, it’s worth considering deactivating or deleting your Facebook account.
Sharing posts like this “just in case” continues the hoax and unnecessarily worries people who might see your post. If you’re not sure about whether you should share something, it’s worth googling the post’s text to check if there are any alerts about it.
If you are worried about how much of your data has been exposed online, you can try our free Digital Footprint scan. Fill in the email address you’re curious about (it’s best to submit the one you most frequently use) and we’ll send you a free report.
We don’t just report on threats – we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your—and your family’s—personal information by using Malwarebytes Identity Theft Protection.
“}]] Read More
Malwarebytes
