Shorter certificate lifespans are beneficial, but they require a rethink of how to properly manage them. Read More
Related Posts

Qakbot Takedown Aftermath: Mitigations and Protecting Against Future Threats
Qakbot Takedown Aftermath: Mitigations and Protecting Against Future Threats
The U.S. Department of Justice (DOJ) and the FBI recently collaborated in a multinational operation to dismantle the notorious Qakbot malware and botnet. While the operation was successful in disrupting this long-running threat, concerns have arisen as it appears that Qakbot may still pose a danger in a reduced form. This article discusses the aftermath of the takedown, provides mitigation Read More
The Hacker News | #1 Trusted Cybersecurity News Site

State-Backed Hackers Employ Advanced Methods to Target Middle Eastern and African Governments
State-Backed Hackers Employ Advanced Methods to Target Middle Eastern and African Governments
Governmental entities in the Middle East and Africa have been at the receiving end of sustained cyber-espionage attacks that leverage never-before-seen and rare credential theft and Exchange email exfiltration techniques.
"The main goal of the attacks was to obtain highly confidential and sensitive information, specifically related to politicians, military activities, and ministries of foreign Read More
The Hacker News | #1 Trusted Cybersecurity News Site
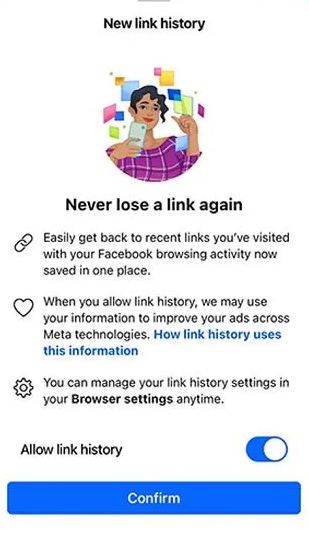
Facebook introduces another way to track you – Link History
Facebook introduces another way to track you – Link History
In what seems like yet another attempt to adapt its platform to prepare for new regulations, Facebook has started rolling out a new feature called Link History.
Link History allows users to view and re-visit links they have visited with their Facebook browsing activity.
Obviously Facebook will tell us that the new feature is for its users’ benefit, but we can see several ways in which this benefits Meta even more. The only positive for me is that it could be a handy option for finding that thing that you saw on Facebook that one time, but you can’t quite remember the details. This gets defeated partially by the fact that users that have Link History enabled report they were unable to see the Link History page at all when looking at Facebook on their laptop.
However, as Facebook tracking goes at least this is an option that you have some control over. On most, if not all, popular websites you’ll find Meta’s and other’s tracking pixels. With an ongoing battle against cookies and other trackers, this may be a new way for Facebook to track its user’s behavior.
With Link History, Facebook now has another separate place where it stores details about the websites you visit along with the settings to control that data. Settings that are, deliberately or not, hard to find and easy to misinterpret.
The company itself says:
“When you allow link history, we may use your information to improve your ads across Meta technologies.”
Translated, this means that they will use the information to provide you with targeted ads.
Recently Meta got sued over coercing users to pay to stop tracking. Organizations concerned about our privacy say that by doing this, Meta has changed the user’s choices from “yes or no” to “pay or okay.”
Research in 2022 showed that in-app browsers inject JavaScript code into third party websites that cause potential security and privacy risks to the user. This resulted in a class-action complaint against Meta in San Francisco’s federal court, alleging the company built a secret workaround to Apple’s safeguards that protect iPhone users from tracking.
So this may be another attempt to follow users around on the web. Unlike on your desktop, clicking a link in Facebook, or Instagram, will open a special browser built into the app, rather than the default browser of the device.
For now, a limited number of Android and iPhone users will see this option appear in the Facebook Mobile Browser. But the company says it will roll out the option globally over time.
How to turn link history on or off
Link history is turned on by default so you will have to opt-out if you don’t want it.
Tap any link inside the Facebook app to open Facebook’s Mobile Browser.
Tap the three dots (more actions) in the bottom right, then tap Go to Settings.
To turn link history on, tap the slider to on (blue) next to Allow link history, then tap Allow to confirm.
To turn link history off, tap the slider to off (grey) next to Allow link history, then tap Don’t allow to confirm.
Note: When you turn link history off, this will immediately clear your link history, and you will no longer be able to see any links you’ve visited. Facebook promises to delete the link history it’s created for you within 90 days.
We don’t just report on privacy—we offer you the option to use it.
Privacy risks should never spread beyond a headline. Keep your online privacy yours by using Malwarebytes Privacy VPN.
Malwarebytes
