The Python Package Index (PyPI) has announced that it will require every account that manages a project on the platform to have two-factor authentication (2FA) turned on by the end of the year. […]
Related Posts
10 Best Automated Penetration Testing Tools In 2024
10 Best Automated Penetration Testing Tools In 2024
Automated penetration testing, known as vulnerability scanning, uses software to detect security flaws in networks, websites, applications, and cloud infrastructure.
The process of assessing security threats in a system using automated security tools is known as “automated penetration testing” (“vulnerability scanning”). Penetration testing detects security problems in your company’s web-facing assets, such as websites and subdomains.
A successful pentest identifies problems, establishes potential ways to exploit them, and predicts the repercussions on the application under test.
Automated penetration testing is less expensive than manual testing and can give results in seconds or minutes.
Which Tool Is Used For Penetration Testing?
Businesses should focus more on information security. It must transcend the domain of strictly technological issues and permeate organizational culture.
Security weaknesses can be found throughout your digital platforms, making it unavoidable for you to be compromised. As a result, a pen testing tool is necessary.
Pentesters and ethical hackers utilize penetration testing technologies to imitate real-world attacks without taking risks, testing the computing infrastructures’ robustness. They are particularly effective at protecting a company from unidentified or “zero-day” threats.
Penetration testing tools include Netsparker, Wiresharker, Metasploit, Aircrack, Intruder, Etercap, Zed attack proxy, Scapy, Nessus, AppKnox, and BurpSuite.
10 Best Automated Penetration Testing Tools in 2024
Intruder – Cloud-based vulnerability scanner for automated security assessments and continuous monitoring.
Autopsy and The Sleuth Kit – Digital forensics platform for analyzing hard drives and mobile devices.
Metasploit – Comprehensive penetration testing framework for discovering, exploiting, and validating vulnerabilities.
Ettercap – Network security tool for man-in-the-middle attacks and network protocol analysis.
Zed Attack Proxy – Open-source web application security scanner for identifying vulnerabilities in web apps.
Scapy – Packet manipulation tool for network discovery, packet crafting, and network protocol testing.
Acunetix – Automated web vulnerability scanner for identifying and resolving security issues in web applications.
AppKnox – Mobile application security testing tool for identifying and fixing vulnerabilities in mobile apps.
BurpSuite – Integrated platform for performing security testing of web applications, including automated scans.
Wireshark – Network protocol analyzer for real-time network traffic capture and deep packet inspection.
10 Best Automated Penetration Testing Tools Features
Best Automated Penetration Testing Tools
Features. Stand-Alone FeaturePricingFree Trail / Demo 1. Wireshark
Network Protocol Analyzer
Interactive Traffic Browsing
Detailed Information on Network Traffic
Troubleshooting and Network Analysis
Supports Hundreds of Protocols
Open SourceContinuous vulnerability scanning and automated security assessments.Starts at $119/monthYes2. Autopsy and The Sleuth KitLook at the metadata
Hashing a file
Detection of deleted files
Carving out data
Look at the registry
Image editing on a diskDigital forensics for detailed file system investigations.FreeNo3. Ettercap
MITM stands for “Man in the Middle” strikes.
Getting network packets
Analysis of protocols
There are two kinds of network scanning:
Spoofing the ARP
Spoofing DNSComprehensive penetration testing framework for exploit development.Starts at $2,000/yearYes4. MetasploitMaking and testing exploits
Creating a payload
Scan for weaknesses
After-the-fact parts
Control and management from a distance
Attack databaseNetwork security tool for man-in-the-middle attacks.FreeNo5. Zed Attack ProxyGetting caught in a web
Checking out web applications
Active searching
Support for authentication
Managing a sessionWeb application security scanner for finding vulnerabilities.FreeNo6. ScapyTests of protocols
Functions of Traceroute
Making custom protocols
Sending and getting packets
Analysis of network traffic
Support for IPv6Powerful packet manipulation and network traffic analysis tool.FreeNo7. AcunetixCross-site scripting (XSS) discovery
Detection of SQL injection
Detection of directory traversal
Prioritization of vulnerability
Reporting on compliance
The API testing optionsSecurity checks on mobile apps
Automatically finding security holes
Look at the code
Help with manual testing
Checks for compliance
Security alerts in real-timeStarts at $4,500/yearYes8. AppKnoxSecurity checks on mobile apps
Automatically finding security holes
Look at the code
Help with manual testing
Checks for compliance
Security alerts in real timeMobile application security testing with automated vulnerability detection.Custom pricing availableYes9. BurpSuiteChecking out web applications
Getting on hands and knees
Scan for weaknesses
Break-in tool
Repeater device
tool sequencerIntegrated platform for web application security testing.Starts at $399/yearYes10. intruder Intrusion Detection System
Real-Time Monitoring
Comprehensive Threat Data
Security Incident Analysis
Supports Multiple Security Protocols
Open SourceNetwork protocol analyzer for in-depth traffic inspection.FreeNo
1. Intruder
Intruder
One of the top automated tools for penetration testing is Intruder.
Avoid costly data breaches using a vulnerability scanner like Intruder to detect cyber defense weaknesses in your digital infrastructure. Intruder provides enterprise-level cyber security without complexity with hundreds of automated security checks.
Intruders actively find new threats and offer a unique threat interpretation method that simplifies vulnerability management, saving you time. AWS, Google Cloud, and Azure cloud connectors can synchronize your systems to avoid missing details.
The attacker looks for application flaws, configuration vulnerabilities, and unpatched security gaps. Just add your aim for actionable results. The intruder utilized the same scanning engine as banks and governments worldwide.
Why Do We Recommend It?
Intruder offers fast support for program use and technical concerns.
Intruders constantly scan targets and reveal weaknesses instantly.
Network, online applications, and cloud configuration scanning help intruders uncover security holes.
Attackers check OS, network, web app, and database vulnerabilities.
Intruders utilize innovative tactics to eliminate false positives, verifying security shortcomings.
Use Intruder with your IDE, bug tracker, or collaboration service.
Intruder reports describe vulnerabilities, severity, and fixes.
What is Good?What Could Be Better?1. Small-footprint internal hardware improves performance.1. Information in reports could be expanded.2. To protect you, it constantly checks the attack surface.2. cannot search a target’s file system for susceptible data.3. Identification of a new vulnerability3. The distribution of internal agents continues to be largely manual.4..An intruder searched server fleets for external vulnerabilities.
Demo video
Price
You can get a free trial and personalized demo from here.
2. Autopsy And The Sleuth Kit
Autopsy and The Sleuth Kit
You can quickly and effectively analyze hard drives and smartphones with the help of the user-friendly GUI-based program known as Autopsy. Because of its plug-in architecture, you can find supplemental modules or create your own in Python or Java.
The Sleuth Kit is a C library and command line toolset that lets you examine and extract files from disk images. It is utilized in Autopsy and numerous other forensics software programs, both open-source and for-profit.
With some modules included right out of the box and others available from third parties, Autopsy was created to be an end-to-end platform.
The Sleuth Kit’s tools have an Autopsy graphical interface, making investigating easier. It is compatible with GPT disks, Sun slices (Volume Table of Contents), Mac partitions, BSD partitions (disk labels), and DOS partitions.
Why Do We Recommend It?
Investigators can duplicate storage media without damaging data with Autopsy and The Sleuth Kit’s forensic disk images.
These apps test NTFS, FAT, Ext2/3/4, HFS+, etc.
Autopsy and The Sleuth Kit search files, names, and unallocated keyword space.
Using metadata, investigators can determine a file’s creation date, last change date, and previous user, as well as write access.
Autopsy and The Sleuth Kit restore missing or corrupted files from unallocated storage via file carving.
The tools can diagnose numerous OS and app faults.
Investigators can produce extensive reports using the Sleuth Kit and Autopsy.
You may expand Autopsy and The Sleuth Kit with plugins and modules.
What is Good?What Could Be Better?1. Wizards guide you through the straightforward installation process.1. New data will prevent file recovery from the hard drive. 2. In a single tree, all outcomes are located.2. As storage capacities increase, processing power for digital information is scarce.3. The app’s autopsy feature lets Users see films and photographs without an external viewer.3. sometimes identify a gadget but not its user.4. Sleuth kit examines disk images and raw
Demo video
Price
You can get a free trial and personalized demo from here.
3. Ettercap
Ettercap
The free and open-source tool ettercap can support man-in-the-middle attacks on networks. It can also be used for computer network protocol analysis and security auditing.
Additionally, it enables the virtual, real-time diversion and modification of data. It can write packets back onto the network after they have been captured, offers a variety of tools for network and host analysis, and supports active and passive protocol analysis.
Ettercap can actively listen to well-liked protocols, intercept network traffic, and capture passwords.
Because it supports network traffic analysis, the most typical use of ettercap is to set up man-in-the-middle attacks using ARP (Address Resolution Protocol) poisoning.
Either an ethical hacker or penetration tester needs to have ettercap in their toolbox
Why Do We Recommend It?
Packet capture and network sniffing with Ettercap reveal network protocols and sent data.
Ettercap is notable for its man-in-the-middle attacks.
Ettercap examines protocols thoroughly.
Use Ettercap aggressively or passively.
Ettercap supports ARP spoofing and poisoning.
By accepting plug-ins, Ettercap can add new features and capabilities.
It may collect or alter only particular network packets using filters.
Ettercap’s remote control lets you run and monitor it from another computer.
What is Good?What Could Be Better?1. Ettercap has a nice UI and CLI.1. Software source compilation requires several dependencies and developer libraries.2. ethical hackers can efficiently perform a session hijacking attack.2. Both Windows 10 and the 64-bit architecture are incompatible with it.3. Adding plugins expands its features.3. Ettercap requires pre-installation on a target network computer..4. Specific endpoint isolation methods are given.
Demo video
.
Price
You can get a free trial and personalized demo from here.
4. Metasploit
Metasploit
A computer security initiative called the Metasploit Project conducts penetration testing, assists in developing IDS signatures, and disseminates knowledge about security gaps.
Using the robust Metasploit framework, cybercriminals, and ethical hackers can explore systemic vulnerabilities on networks and servers.
Due to the partnership between the open-source community and Rapid 7, Metasploit assists security teams in managing security assessments, enhancing security awareness, and verifying vulnerabilities more than just.
Metasploit gathers 1677+ exploits for 25 platforms, including Android, PHP, Python, Java, and others. The framework supports around 500 payloads. Metasploit contains exploits, payloads, encoders, listeners, shellcode, auxiliary operations, post-exploitation code, and nops.
Why Do We Recommend It?
Metasploit’s extensive library of pre-built exploits and payloads may target and exploit computer vulnerabilities.
Metasploit’s post-exploitation modules let you do more after exploiting a system.
The Metasploit repository contains many remote and local vulnerabilities.
After exploiting a system, Metasploit can deliver many payloads to the vulnerable PC.
Metasploit’s Social Engineering Toolkit enables social engineering attacks.
The automated exploitation modules in Metasploit ease vulnerability exploitation.
Metasploit can record penetration testing thoroughly.
What is Good?What Could Be Better?1. Metasploit is free because it is open source.1. System crashes can happen from Metasploit misuse.2. Updates are made to the exploit database.2. option for managing payload.3. various projects have their workspace.3. Few GUI-based tools exist since the CLI is so popular.4. Automation of manual testing and exploits can complete processes that took days and hours.
Demo video
Price
You can get a free trial and personalized demo from here.
5. Zed Attack Proxy
The OWASP Foundation strives to increase software security through community-led open-source software projects, tens of thousands of members, hundreds of chapters worldwide, and local and international conferences.
An open-source security program called Zed Attack Proxy, created in Java and released in 2010 scans web applications and identifies vulnerabilities.
Zed Attack Proxy can find any web server’s vulnerabilities and try to fix them. It is made for people with various security experiences, making it perfect for developers and functional testers just starting penetration testing.
ZAP builds a proxy server for website traffic. The tester can also change the message’s content in any terms to test the web application’s vulnerabilities. Automatic scanners detect and resolve website vulnerabilities.
Why Do We Recommend It?
ZAP is a proxy that intercepts and modifies web app-user conversations.
It supports active and passive scanning.
ZAP has a robust API for scripting and automation.
ZAP delivers a detailed list of concerns for vulnerability management.
It makes managing sessions and authentication for safe online application testing easy.
ZAP generates detailed scan results and vulnerability reports.
The strong OWASP community ensures ZAP updates and development.
What is Good?What Could Be Better?1. It supports Mac, Windows, and Linux in 29 languages.1. The software uses a resource-intensive forced browser.2. Installation choices include standalone apps and daemons.2. The lengthy, disorganized report has no output.3. Worked across all operating systems 3. The backend system’s inability to properly authenticate users.4. Examine every page for vulnerabilities, then highlight the affected code.
Demo video
Price
You can get a free trial and personalized demo from here.
6. Scapy
Scapy
It can match requests and responses, send packets on the wire, capture them, forge or decode packets of various protocols, and do much more. The Python program Scapy allows one to send, sniff, analyze, and forge network packets.
Most conventional tasks, including network discovery, unit testing, probing, scanning, tracerouting, and attacks, can be handled quickly.
Despite being a command-line tool, it can still interface with various other applications to provide visualization, such as Wireshark, GnuPlot for graphs, graphviz, or VPython for interactive display.
In addition, it excels at many other specialized tasks that most other tools cannot complete, such as sending erroneous frames, injecting custom 802.11 frames, and combining methods.
Scapy’s paradigm is a Domain-Specific Language (DSL) that allows for the quick and effective description of any type of packet.
Why Do We Recommend It?
Scapy generates and modifies network packets at a low level.
Network scanning and discovery are feasible with Scapy.
Scapy reads live and recorded packets.
Decoding packets from several network protocols is built into Scapy.
Scapy works with Wireshark.
Python scriptability lets Scapy be utilized in automation workflows or larger Python scripts.
Scapy can support new or modified protocols.
A lively user and programmer community supports Scapy development and maintenance.
What is Good?What Could Be Better?1. Scapy runs on Linux, Windows, OS X, and most Unixes using libpcap.1. Unable to manage numerous packets at once2. Runs several unit tests with varied parameters between two limitations.2. limited support for some complex protocols3. Scapy, a Python packet manipulation tool, is flexible.3. Python is used to write Scapy, which has numerous abstraction layers but is not fast.4. Send, sniff, analyze, and forge network packets with Scapy.
Scapy can be downloaded from GitHub or PyPI using the following link: https://scapy.net/download/
Demo video
Price
You can get a free trial and personalized demo from here.
7. Acunetix
Acunetix
As application layer attacks have become more prevalent, Acunetix Web Vulnerability Scanner was developed as a web application security testing tool. It is intended to help web developers and network administrators protect servers and applications from various threats.
Acunetix WVS conducts a series of attacks against a website to perform a security audit. Then, it provides detailed reports of any vulnerabilities, including suggestions for fixing them.
With the tool, you can make a target list of websites to divide into subcategories. Then, you must enter several options, including the scan speed and your login details.
Acunetix can identify more than 7,000 vulnerabilities using a combination of DAST and IAST (Interactive Application Security Testing) scanning. Its three tenets are Find, Fix, and Prevent.
Why Do We Recommend It?
Acunetix automatically scans online application code, server configurations, and other components for security issues.
It uses DeepScan, a black-box-gray-box testing method.
An Acunetix AcuSensor sensor must be installed on the web app server.
Acunetix provides detailed reports on vulnerabilities, their severity, and how to remedy them.
It integrates with Jira and Jenkins for easy bug reporting and collaboration.
Acunetix checks web API safety.
With Acunetix’s DevOps help, security testing is easy to integrate into software development.
Acunetix’s ongoing scanning and monitoring protect online apps.
What is Good?What Could Be Better?1. Quickly relaunching scans on updated website areas.1. Supports importing state files from various well-known application testing tools.2. Most critical and well-publicized vulnerabilities are covered.2. Supporting multiple endpoints is not its strongest suit.3. Includes features beyond vulnerability scanning.3. In current workplace apps, multiple URLs cause authentication issues.4. Enables importing state files from popular application testing tools.
You can get a free demo of the Acunetix tool from here – https://www.acunetix.com/web-vulnerability-scanner/demo/
Demo video
Price
You can get a free trial and personalized demo from here.
8. AppKnox
AppKnox
With the help of a system and a human approach, Appknox, the most potent plug-and-play security platform in the world, enables Developers, Security Researchers, and Businesses to create a safe and secure mobile ecosystem.
Appknox is committed to providing mobile app security testing to support businesses in achieving their goals now and in the future. It has experience in various industries, including FMCG, BFSI, payments, gaming, transportation, and logistics.
It is a security solution that has received recognition from Gartner. It is trusted and used by companies with mission-critical systems that depend on top-notch security to deliver long-lasting, high-value goods and services.
Without slowing down the SDLC, its remediation framework assists in understanding and excluding the current vulnerabilities.
Why Do We Recommend It?
Appknox can discover mobile app binary security issues using static analysis.
It simulates mobile app user behavior for dynamic analysis.
Appknox evaluates API safety.
It monitors mobile apps 24/7 to help organizations find security problems.
Appknox can provide detailed reports on vulnerabilities, severity, and fixes.
Appknox integrates with Jira and Slack to simplify collaboration and problem-solving.
It analyzes mobile app reputations for vulnerabilities in third-party libraries, SDKs, and services.
What is Good?What Could Be Better?1. Allow multiple team members and app assignments.1. After the mobile app scans, report because only PDF downloads, not Excel.2. Appknox DAST and API can help developers meet deadlines.2. Test turnaround time can be decreased, especially for retests.3.Users can choose engagement tactics and deployment types to fit their security concerns.3. Users can choose engagement tactics and deployment types to fit their security concerns.4. A top security penetration testing team, industry-recognized test scenarios, and an accessible tool.
You can download a free trial of Appknox by visiting the following website: https://www.appknox.com/free-trial?hsCtaTracking=96929d0d-9658-4b1c-975a-2ad052a5f7ae%7C30cba294-7cb5-47c3-8f36-f6793b44c9a4
Demo video
Price
You can get a free trial and personalized demo from here.
9. BurpSuite
BurpSuite
Burp Suite is a fully functional web application attack tool capable of performing almost all the tasks necessary to conduct a penetration test on a web application.
Burp Suite has many tools, such as a scanner, spider, proxy, intruder, repeater, sequencer, decoder, and extender. It is created by a business called Port Swigger, which is also the pseudonym of the company’s founder, Dafydd Stuttard.
It is the tool that web app security experts and bug bounty hunters use the most. It is more suitable because it is simpler to use than free alternatives like OWASP Zap.
BApps are add-ons that can be installed to increase the functionality of Burp Suite, which aims to be an all-encompassing collection of tools.
Why Do We Recommend It?
Burp Suite’s powerful scanner can quickly discover SQL injection, XSS, CSRF, and other web application problems.
It can intercept and alter client-server HTTP/HTTPS conversations as a proxy.
Burp Suite’s web application crawler automatically maps website architecture.
Burp Suite’s Intruder tool automates vulnerability testing by sending a target many well-prepared queries.
Burp Suite’s Repeater lets users manually edit and resend queries.
The Sequencer tool in Burp Suite assesses application data like session tokens for unpredictability.
Burp Suite’s Decoder tool can decode, encrypt, and change many modern web application data types.
Burp Suite users can customize and enhance its structure.
What is Good?What Could Be Better?1. checking for vulnerabilities in a request.1. More creative and representative software presentation is needed.2. Best and most basic data security pentesting tool.2. Plugin updates must be done manually without network access. 3. Works well without a private internet network.4. automated bulk scanning and simulations.
Burp Suite is available in three editions: a free community edition, a professional edition that costs $399/year, and an enterprise edition that costs $3999/year.
You can download the community edition for free.
Demo video
Price
You can get a free trial and personalized demo from here.
10. Wireshark
Wireshark
Gerald Combs started creating Ethereal, the product’s original name, in late 1997 in response to his need for a tool for detecting network issues. The project was renamed Wireshark in May 2006 due to trademark issues.
It develops communication protocols, network troubleshooting, and analytic software. Network administrators, engineers, hobbyists, and black-hat hackers love Wireshark because it monitors practically all network standards (ethernet, WLAN, Bluetooth, etc.).
This program helps with network analysis and security by analyzing, filtering, and delving into network traffic. We can monitor and filter packets to meet our needs. Ethical hackers explore security holes with Wireshark.
Wireshark is beloved by network administrators, engineers, enthusiasts, and black hat hackers because it offers network monitoring on almost all network standards (ethernet, WLAN, Bluetooth, etc.).
Why Do We Recommend It?
Wireshark can capture and analyze network events on many interfaces in real-time.
Wireshark can analyze pcap and other popular packet capture files.
Due to its broad protocol compatibility, Wireshark can decode and analyze many network protocols.
Wireshark features powerful filtering and searching.
Statistics can be used to analyze network traffic in Wireshark.
Wireshark excels in VoIP traffic analysis.
An expert system in Wireshark can identify and report network data anomalies.
What is Good?What Could Be Better?1. Network analysts can help find and fix delays.1. neither create nor modify packets.2. Export packets for other tools.2. Packets cannot be sent 3. reveals the packet-creating protocol.3. Not allowed to change or manipulate any networked data or objects.4. permits packet filtering, grouping, and sorting.
Link to download Wireshark on Windows.
On Linux – you will find Wireshark in its package repositories
Users can download Wireshark for free and use it without purchasing a license.
Demo video
Price
You can get a free trial and personalized demo from here.
Frequently Asked Questions
There are three primary penetration testing techniques, each varying in the amount of information given to the tester prior to and throughout the evaluation.
Black Box Penetration Testing
Black box penetration testing involves testing systems without knowledge of the systems being tested.
Inquiring about the intended network or system is something he is interested in doing.
Grey Box Penetration Testing
In this testing, a tester typically provides limited or incomplete information about the system’s program.
It could be regarded as an attack by an outside hacker who had illegally accessed a company’s network infrastructure documents.
White Box Penetration Testing-
This testing is thorough because testers can access a wide range of system and/or network-related data, including IP addresses, source code, OS information, and schema.
The typical interpretation is that it represents a simulation of an attack by an internal source.
Testing in a glass box, a transparent box, or an open box are additional names fo
While penetration testers can employ a dynamic or static approach, DAST uses a dynamic approach when testing web applications.
Continuous testing and scanning of an application is made possible by the availability of DAST tools.
Rarely, typically every three months or once a year, are manual penetration tests conducted.
While most penetration tests are manual (although there is a growing category of automated penetration testing tools), DAST tools are automatic.
The development of new apps every day demonstrates how far technology has come.
DAST tools can produce false positives, which may find problems that aren’t actually vulnerabilities.
False positives cannot occur during penetration testing by definition.
Modern DAST tools, however, close this gap and deliver reports with zero false positives by utilizing artificial intelligence (AI) and fuzzing tools.
The post 10 Best Automated Penetration Testing Tools In 2024 appeared first on Cyber Security News.
Google ad for Facebook redirects to scam
Google ad for Facebook redirects to scam
[[{“value”:”
Today, we are looking at a malicious ad campaign targeting Facebook users via Google search. It is well-known that tech support scammers attract new victims by buying ads for certain keywords related to their audience.
What is perhaps less known is how it is even possible to impersonate top brands and get away with it. We will try to respond to the ‘how they do it’ and the ‘why is Google allowing this’ questions.
Such malvertising attacks are not new and the damage they cause to consumers is growing every day. There is no one way to stop all of them, but public reporting will hopefully drive the point home that this needs to be addressed just like other types of fraud or malware.
We have reported the malicious advertiser to Google, but at the time of publishing this campaign was still on.
Malicious ad campaign for Facebook
Justin Poliachik did what many people would do, he opened up a Google search, typed facebook and clicked on the top result. In the video below, he summarizes what happened next:
Thanks to Justin for the shoutout to our blog and explaining what went down! Not sure if Justin was joking, but we don’t believe AI is going to fix malvertising, at least not for the next little while. Instead, we are going to look into more details about one particular technique. In our view, this is actually where the abuse happens the most, and where things could be improved.
Two paths make cloaking
As we said, Google seems to have a problem with brand impersonation that may not be easy to solve. We have reported such cases several times before with pretty much the same techniques.
How can Google differentiate a legitimate affiliate from a malicious actor? There are a number of data points about the advertiser via their account: user profile, payment method, budget, etc. We are not privy to those details, but they can certainly help when it comes to fraud.
More importantly, there is the ad itself: vanity URL, display text, tracking template, final URL. What happens when you click on the ad? Are you actually redirected to the URL claimed in the ad? This is a feature that appears to be so easy to abuse, and yet remains unfixed.
In the video below, we walk you through the classic tale of cloaking:
Cloaking is an old technique and in many ways can be used for legitimate purposes. After all, one needs to be able to detect real humans and not bots or crawlers for their hard-earned ad dollars budget.
Threat actors have long identified such services as very helpful tools for their malicious campaigns. True, they, like others don’t want robots, but they also don’t want Google’s scanners or security researchers to expose their malicious schemes.
Under the hood
This part is a little more technical, but integral in understanding how malvertising works. As mentioned in the video above, cloaking allows to deliver two different experiences. Genuine humans can be detected from a number of factors: IP address, browser fingerprinting, etc.
A click tracking service can be used to analyze traffic, collect data, etc. All in all, such services are useful in and of themselves, but they can also easily be abused by bad actors. Within the Google ad ecosystem, advertisers will place their URL as a tracking template, and the rest will be handled outside of Google.
One thing that’s interesting is how scammers will abuse the click tracking service as well! All they have to do is redirect to another “legitimate” domain they control and from there decide on the final destination URL.
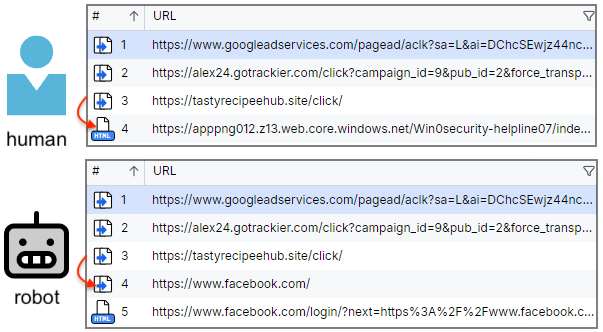
We can see in the image below that final redirect, which is either the scam page or the actual Facebook site:
Safeguarding your online experience
We have seen these malicious ads for years and years. It would be unfair to say that no action has ever been taken, but there is room for improvement. Individual reports from victims are not always actioned based on our experience and that of others. This is frustrating because it appears as if those individual experiences do not matter in the grander scheme of things.
Security vendors also struggle with these scams. Chasing infrastructure from one host to the next or having trouble blocking URLs that abuse legitimate providers is a real thing.
As a user you can protect yourself in various ways:
Beware of sponsored results
Block ads altogether
Recognize scam pages as fake
If you want the piece of mind and have all this covered for you, download our Malwarebytes Browser Guard extension available for different browsers.
“}]] Read More
Malwarebytes

Decoy Dog: New Breed of Malware Posing Serious Threats to Enterprise Networks
Decoy Dog: New Breed of Malware Posing Serious Threats to Enterprise Networks
A deeper analysis of a recently discovered malware called Decoy Dog has revealed that it’s a significant upgrade over the Pupy RAT, an open-source remote access trojan it’s modeled on.
"Decoy Dog has a full suite of powerful, previously unknown capabilities – including the ability to move victims to another controller, allowing them to maintain communication with compromised machines and remain Read More
The Hacker News | #1 Trusted Cybersecurity News Site
