Cybersecurity researchers have discovered what they said is the first known malicious Microsoft Outlook add-in detected in...
Security Aid
A surge in LummaStealer infections has been observed, driven by social engineering campaigns leveraging the ClickFix technique to...
Campaign combines stolen Telegram accounts, fake Zoom calls and ClickFix attacks to deploy infostealer malware
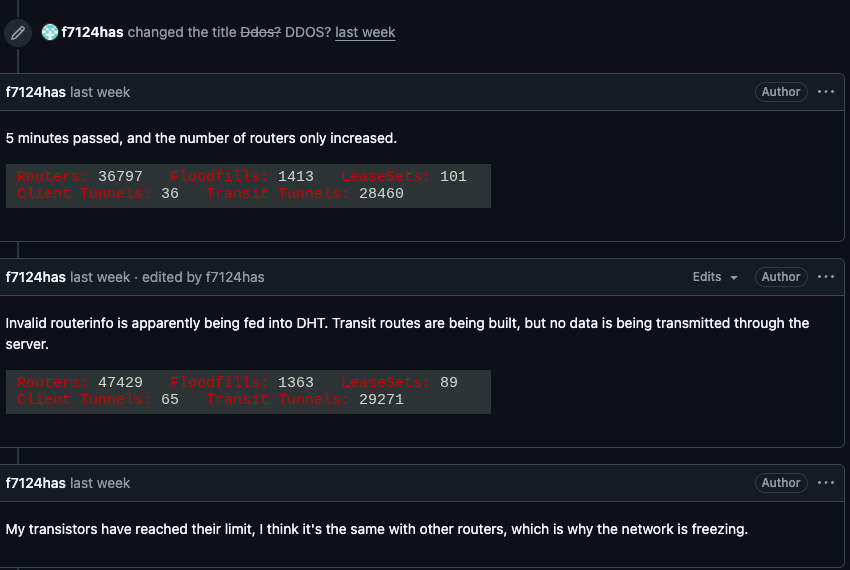
For the past week, the massive "Internet of Things" (IoT) botnet known as Kimwolf has been disrupting...
Gain practical insights on balancing security, user experience, and operational efficiency while staying ahead of increasingly sophisticated...